EDIT 20/12/2021: You now only need to run one script. The new vc_log4j_mitigator.py script merges both remove_log4jclass.py and vmsa-2021-0028-kb87081.py. No further action is required if you already ran those two.
EDIT 17/12/2021: A new script is required to remediate Analytics Service and CM Service. You now need to download remove_log4jclass.py available in KB87081 and run it at the end after running vmsa-2021-0028-kb87081.py.
If you don’t know about the Log4j vulnerability yet (CVE score 10/10), it probably means you don’t need to worry about it (or live in a cave). Anyway, I won’t bother writing an introduction on Log4j in this blog since it has been literally everywhere on the internet. In this blog we will cover the mitigation of Log4j for vCenter Server and Nakivo B&R.
Nakivo Backup and Replication v10.5.1
Following the tsunami of exploit attempts of Log4j across the globe, all software vendors leveraging it have been scrambling to roll out a patch in order to mitigate the vulnerability. It is even significantly more critical when it comes to backups as there are already reports of Ransomware leveraging the vulnerability. In case of an encrypting attack, backups will be your last line of defense and if they are impacted by the ransomware, this will make the recovery very complicated if not impossible.
Nakivo was quick to react and distributed Nakivo Backup and Replication v10.5.1 for which the main purpose is to mitigate the Log4j vulnerability. However, a couple extra changes were included such as support for vSphere 7.0.3 and QTS 5.0 OS as well as other minor product usability issues.
You can either update your appliance from the Web Console or download the updater component, upload it to the appliance and apply it manually in command line. Regardless of the update path you choose to go for, don’t wait to update your Nakivo Servers and protect your backups now !
VMware vCenter Server
Most VMware products are impacted by it since they use Java quite a lot, this is detailed in VMSA-2021-0028. You’ll find links to workarounds for each product, a patch will also be added when they release a fixed version.
Now, the Log4j vCenter workaround is described in KB87081 but there is also a Python script that will automate all of that for you. And don’t worry the script is distributed by VMware themselves.
- Head over to KB87088 and download the script.
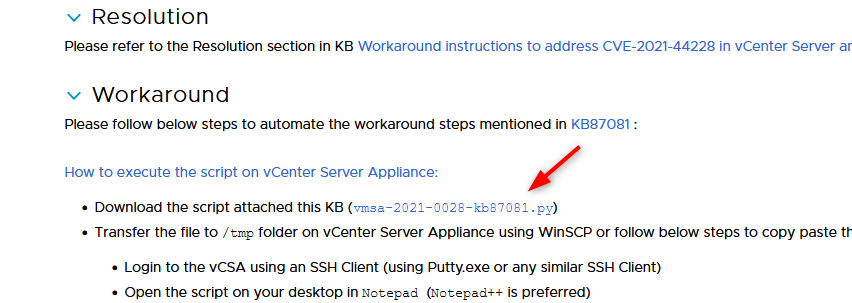
- Copy the script to your vCenter appliance in /tmp. Either use WinSCP or copy/paste it in a file.
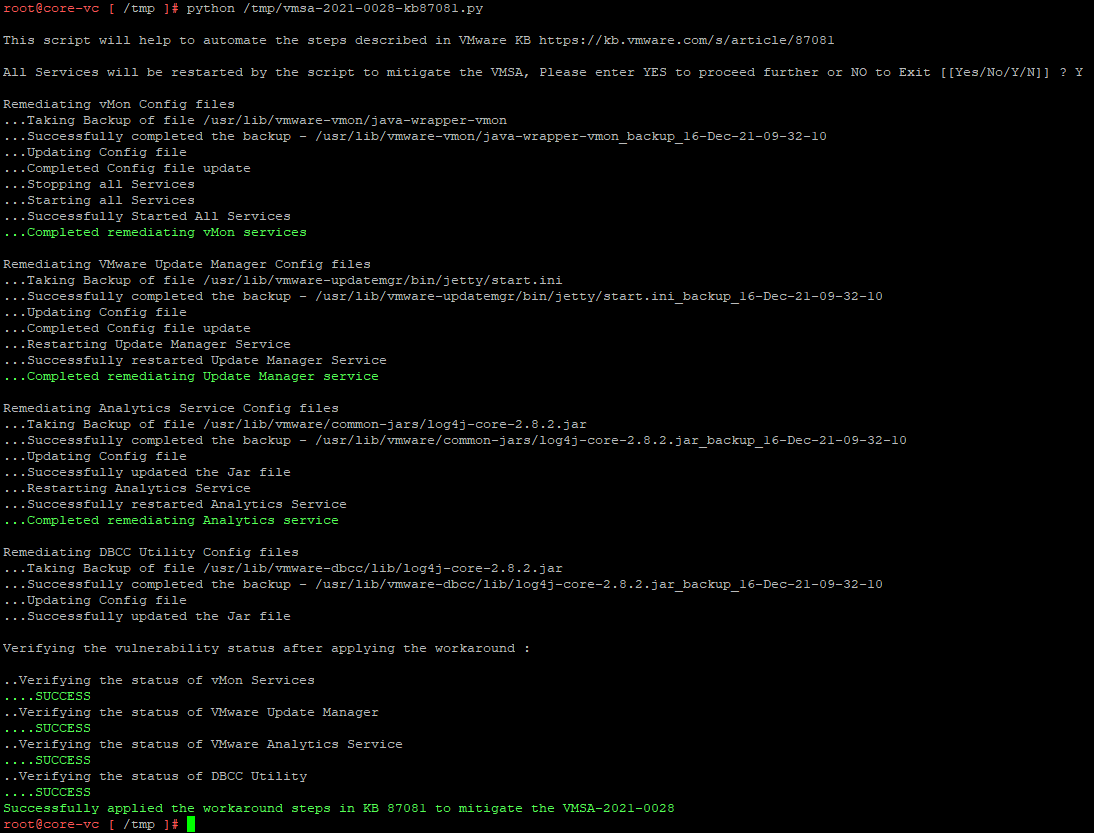
- Execute the script like so.
Note that you will have to confirm that you want to restart all the services so you may to ensure that this will not disrupt other ongoing operations.
python /tmp/vmsa-2021-0028-kb87081.py
- This is the output on my vCenter 7 Update 3.
- EDIT 17/12/2021: Download remove_log4jclass.py from KB87081 and run it to remediate the Analytics Service and CM Services.

Regardless, I suggest you subscribe to those KBs and keep an eye out for new developments as things have been moving very fast over the last few days on this front.